Category: Other
-

KnowIT 的故事
当发现公司的知识产权在眼皮底下被员工盗窃,在痛苦和挫折中,我们开始了寻找监控雇员职责、行为的解决方案。于是,KnowIT诞生了。 KnowIT的故事发生在三年之前,我们的创始人突然发现一位已经公司效力三年的项目经理还在使用Skype和一名最近辞职的员工聊天。事情有些可疑,这名已经辞职的员工因为家中有丧事而请假两个月,回来之后觉得心里愧疚而立即提出辞职。 发现蛛丝马迹,公司决定登录当前所有员工使用的电脑、检查他们的Skype通讯记录。 当发现真相时,我们受到了巨大的打击,原来这两个人正在计划盗取完全由我公司开发的知识产权。申请丧假完全是一个诡计,从而可以有充足的时间在外进行他们的计划。更让恼怒的是,当时他们仍然是公司的正式员工、使用公司的资源、领取公司薪水。 确凿的证据就在眼前 — 不仅仅是从他们的信息交流 — 还有包含有知识产权的文件传输,比如; 源代码 用例 所有发票及客户邮件列表 商业计划 销售模式 电子邮件模板 一个网站的PSD花费10万美元 雪上加霜的是,从他们的通讯资料中显示:他们还在尝试拉拢更多的重要员工加入他们的新公司。 不只是令人震惊,还让我们面对着现实的威胁。我们需要立即采取行动,在开除他们之前,监控他们的行为、尽可能获得更多的证据。他们呆的时间越长,盗取的东西会越多。 显然,时间非常紧迫,没有人曾有过监控雇员的经验。公司的CEO亲自在上网寻找可行的方式方法,但结果却令人失望、困惑。几十个网站的查询结果,没有任何有价值的信息。 淘汰了那些几乎无法获得真实信息的产品,淘汰了那些专门刺探别人隐私的产品,还有淘汰了那些功能不全的产品,最后只有两款产品入围。 无奈的是,这两款产品都需要采购大量的设备,建立服务器和进行安装,并且要求预先支付一定的年费;第二种选择更加糟糕,在报价之前,我们必须和他们的销售人员先联络,他们似乎生活在前互联网时代。 时间就这样悄悄地流走了…… 最终的解决方案,由三个人组成了一个团队,从开始组建到完成花费了几天的时间。最终,产品到是可以工作,但结果不是那样令人满意。 到目前为止,最坏的事情是一年之后,系统也被淘汰了、然后就那样被尘封起来。而今,没有人了解如何使用这个系统,所有的硬盘存满了截图、密码忘记了…… 唯一能让我们想起来的是,源源不断的广告邮件来自那开发软件的公司,说:如果我们想要继续使用软件,他们会给我们更高的折扣………
-
История создания KnowIT
KnowIT появился среди боли и разочарования в поисках решения для мониторинга наших сотрудников, когда мы обнаружили кражу нашей интеллектуальной собственности буквально из-под носа. Эта история…
-

La Historia De KnowIT
KnowIT nació desde el dolor y la frustración de nuestra propia búsqueda de una solución de monitoreo para empleados cuando descubrimos el robo de nuestra…
-

จุดเริ่มต้นของ KnowIT
KnowIT เกิดจากการเฝ้าเพียรพยายามหาโปรแกรมติดตามพนักงานที่มีประสิทธิภาพ เพื่อรับมือกับวายร้ายที่อยู่ใต้จมูกของเรานี่เอง เรื่องราวของ KnowIT เริ่มจาก 3 ปีก่อน เมื่อผู้ก่อตั้งบริษัทของเราได้รับรายงานจากผู้บริหารระดับสูงว่าพนักงานที่ทำงานกับเรามานานถึง 3 ปีได้ใช้โปรแกรม Skype ในการพูดคุยกับพนักงานที่เพิ่งออกจากงานไปไม่นาน น่าแปลกที่ว่าพนักงานคนนี้ได้ขอลาออกทันทีที่กลับมาจากการลาพักร้อน 2 เดือนด้วยเหตุผลส่วนตัวที่ไม่มีใครทราบได้ ด้วยความสงสัย เราจึงล็อคอินเข้าไปที่เครื่องของพนักงานที่ยังปฏิบัติงานอยู่กับเราและตรวจสอบข้อมูลบนโปรแกรม Skype กลายเป็นว่า ทั้งสองคนกำลังวางแผนที่จะสร้างบริษัทของตัวเองขึ้นมา โดยลอกเลียนแบบเทคโนโลยีเกือบทั้งหมดที่บริษัทเราใช้เวลาพัฒนามาอย่างยาวนาน การลาพักร้อนที่ผ่านมาก็เหมือนจะเป็นการถ่วงเวลาเพื่อที่จะเตรียมการจัดตั้งทีมงานของตัวเอง ในขณะที่ยังรับเงินเดือนจากทางบริษัทและสามารถเข้าถึงข้อมูลได้อย่างพนักงานทั่วไป หลักฐานที่ได้ชัดเจนและโหดร้ายมาก…
-
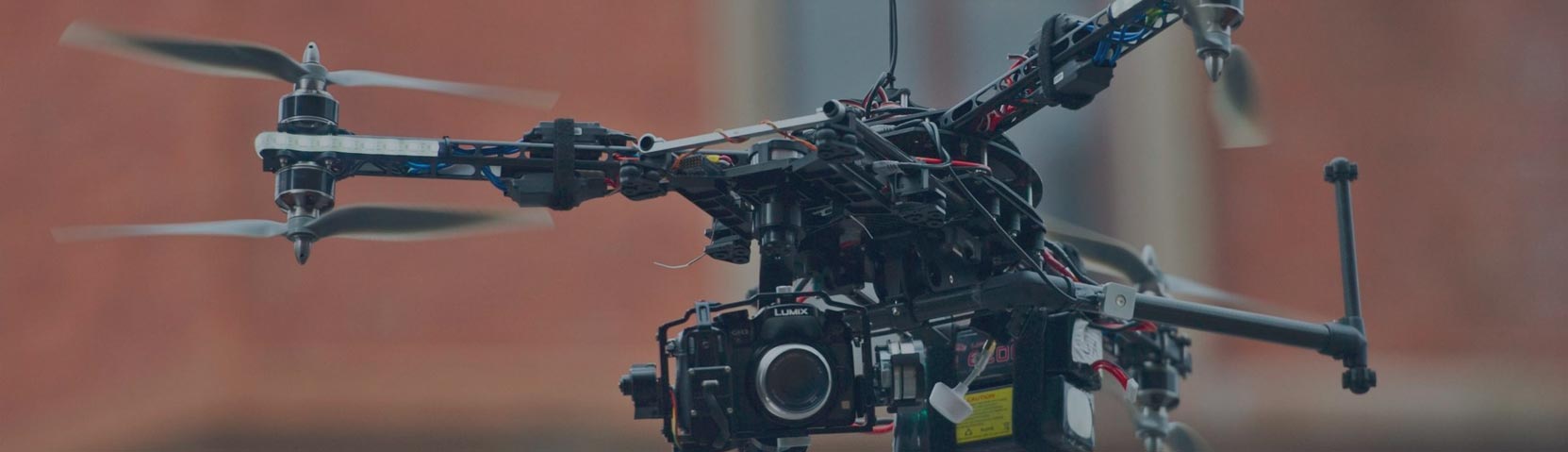
Some of the Worst Ways to Monitor Employees
Monitoring is a key part of management. Employee monitoring can take many forms, from the humble punch clock to sophisticated software. At its best, monitoring…
-

Employee Monitoring in Singapore | What’s Allowed?
If you’re in Singapore and you want to monitor your employees, you’re in luck. The law apparently allows you to keep an eye on workers…
-

How to Monitor Employees’ PCs …Without Going Too Far
We know by now how much sense it makes to monitor employees: for productivity, to protect your networks and to safeguard your intellectual property. But…
-

Canada’s BYOD Guidelines: How They Can Help You
Many governments and organizations are just now realizing the importance of setting up BYOD guidelines to protect themselves against possible data breaches through workers’ devices.…
-

When Can You Read Employees’ Emails?
Most managers would rather not spend their time reading employee emails. Aside from the practice bordering on the creepy, it’s fair to assume employers have…
-

How To Introduce Employee Monitoring To Your Employees
Employee monitoring makes sense. It keeps track of workers’ productivity, prevents hacks and malware from being introduced into systems, and protects sensitive company data. Employer…
-

The New EU Data Protection Regulations: What They Mean for You
The EU is preparing to upgrade its data protection regulations this year, and there are changes in store for employers regarding the protection of employee…
-
The Best Employee Monitoring Software: What’s Right For You?
Trust – difficult to earn and easy to lose, and yet it’s a business imperative – As a manager and business owner, you must earn…
-

What Happens When an Employee Loses a Company Device?
It seems there’s a new headline almost every day: Computers stolen. Data lost. Customers’ security at risk. There’s a surprising amount of data out there…
-

Why startups should monitor employees’ PC / Mobile access
So you’ve launched your Big Idea and your startup is finally off the ground. You have staff and funding, and your office space is up…
-

Employee Monitoring in Hong Kong – What’s Allowed?
It’s easy to see why employers in Hong Kong may want to monitor workers in the wake of a December 2014 survey by the recruiting…
-

Employees: The weak link in your company’s security?
You need employees to run your business. Without them, you’d have to do everything yourself – and let’s face it, you can’t do EVERYTHING. But…
-

What We Can Learn from the Ashley Madison Breach
Legions of wannabe spouse cheaters were exposed to the world in August after a massive data breach of the Ashley Madison website. The website claims…
-

Bring On BYOD! Best Practices for Bringing Your Own Device
Do you know what BYOD is? It stands for “bring your own device,” and it’s the practice of employees using their own phones, tablets and…
-

Why You Need To “Know” If Employees Are Using Cloud Apps
[et_pb_section admin_label=”Section” fullwidth=”on” specialty=”off” transparent_background=”off” allow_player_pause=”off” inner_shadow=”off” parallax=”off” parallax_method=”off” padding_mobile=”off” make_fullwidth=”off” use_custom_width=”off” width_unit=”on” make_equal=”off” use_custom_gutter=”off”][et_pb_fullwidth_post_title admin_label=”Fullwidth Post Title” title=”on” meta=”on” author=”on” date=”on” categories=”on” comments=”on” featured_image=”on”…
-

Employee Monitoring and Productivity: The Positive Correlation
Employee monitoring is not about keeping checks and balances for the sake of company protocol. It is about data protection, compliance and guarding against very…
-

How To Avoid Employee Monitoring Gone Wrong
Cyber-attacks are part of the digital landscape businesses have to navigate today. Running alongside this is the growing need to monitor employees to ensure they…
-

3 More Employee Google Searches To Look Out For
Whilst searching for a sofa for sale during your lunch-break is innocuous enough, employers need to be aware when employee Googling could signal trouble and…
-

Monitoring Mobile Employees for Safety and Efficiency
Most companies that employ a fleet of vehicles use fleet monitoring software to track the location and movement of their cars / trucks / motorbikes…
-
The Story Of KnowIT
KnowIT was born from the pain and frustration of our own search for an employee monitoring solution when we discovered the theft of our intellectual…
-

When Your Employees Leave What Leaves With Them?
Lock the doors against malware attacks; batten down the hatches against cyber warfare; pull up the drawbridge to prevent online criminals battering down the door…
-
Monitoring Vs. Blocking: How to Ensure Productive Employee Internet Browsing
There was some sobering news in a 2014 survey about wasting time at work: Employees spend a lot of time in non-work-related web browsing, with…
-

Want to Avoid Data Breach Liability? Monitor Your Employees
With data breaches on the rise financial liabilities and burdens are also increasing, not just for headline-grabbing incidents, but everyday attacks on SMBs. Alongside this,…
-

Data Breaches – The Rising Threat
Data is one of the most valued assets of any business and yet breaches are increasing at an alarming rate, with threats often closer to…
-
How To Stop Porn From Killing Your Business
It seems like a no-brainer, but porn at work is still an issue employers need to address. Apparently, the temptation is too strong for some…
-

The Legality Of Employee Monitoring | Position Paper
[et_pb_section fullwidth=”on” specialty=”off” transparent_background=”off” allow_player_pause=”off” inner_shadow=”off” parallax=”off” parallax_method=”off” padding_mobile=”off” make_fullwidth=”off” use_custom_width=”off” width_unit=”on” make_equal=”off” use_custom_gutter=”off”][et_pb_fullwidth_post_title admin_label=”Fullwidth Post Title” title=”on” meta=”on” author=”on” date=”on” categories=”on” comments=”on” featured_image=”on” featured_placement=”above”…
-

Data Theft By Employees: The Enemy Within
Viruses, spyware, adware, phishing and hacking, not to mention spam delivering fraudulent activities through malware and organized criminal activities. The threats from cyber criminals is ever…
-

Ethical Employee Monitoring – A How To Guide
We live in a world where everyone is watching and everyone is being watched. Technological advancements have changed the way we communicate, how we store…
-

3 Employee Google Searches You Can’t Ignore
The promise of endless knowledge at one’s fingertips is probably the most influential achievement of the past 20 years. It’s very hard to imagine now…
-
Sexting on the Company Phone: An Employer’s Perspective
Here’s something workers should already know: Don’t use a work phone to send dirty pictures or texts. …But we humans sometimes fall prey to temptation,…
-

How Much is Facebook Costing You?
Social media might keep us more connected, but when it comes to workplace productivity, sites like Facebook and Twitter could prove to be a real…
-

Are Your Employees Looking for Another Job?
Business is about people, and getting the right employees in place is vital for any company’s success. Losing a member of staff to a competitor…
-

Monitoring Employees? Only Cloud Storage Cuts It
Many employers have realized the benefits in monitoring employees’ computer use, benefits which include; keeping workers focused, preventing intellectual property theft, helping to avoid lawsuits or…
-

Trends in PC Tracking at Work
Employee Tracking Is on the Rise. Infact, a recent Bloomberg News story said as many as 20 companies are selling tools to keep an eye on…
-

Key Elements of Employee Monitoring Software
For many employers, it’s not enough just to monitor employee productivity. They must also make sure their workers don’t use company-issued devices inappropriately or illegally.…
-

Protect Yourself from Employees’ Illegal Communications
A frequently overlooked but potentially devastating aspect of Thai law makes employers liable for illegal communications sent by their workers. Thailand’s Civil and Commercial Code…
-

Do Freebies Cut It For Employee Monitoring?
For many employers, it’s not enough just to monitor employee productivity. They must also make sure their workers don’t steal their intellectual property or use…
-

Is Employee Monitoring a Productivity Hack?
As cybercrime and hacking gradually rise to the forefront of corporate concerns, companies both large and small are increasingly turning to technology in order to…
-

HIPAA Compliance Challenges That SMS Presents To Healthcare Facilities
Are you aware of the HIPAA Compliance challenges that SMS messages present to Healthcare Facilities? We have partnered with Rackspace® to bring KnowIT to the…
-

Five Productivity-Killing Websites Your Team Should Stay Off
The internet has revolutionized work in ways we couldn’t have dreamed of just a few years ago, yet all that connectedness brings a lot of…
-
Insider theft in the news again
Yes, sadly it’s yet another “insider theft lawsuit” to add to the list… This one has an interesting spin on it, in that, the “five” are…
-

Bring your own device: what does it really mean for your business?
When it comes to your workplace, chances are you have come across the term ‘bring your own device.’ If you haven’t, this is still a…
-

Could you have seen IT coming with KnowIT?
Congratulations! You’ve been promoted to Supervisor! Of all the candidates, both internal and external, you stood out as most qualified and most ready for the…
-
KnowIT Upcoming Features
[et_pb_section admin_label=”section”][et_pb_row admin_label=”row”][et_pb_column type=”1_4″][et_pb_image admin_label=”Image” src=”https://blog.digitalendpoint.com/wp-content/uploads/2015/12/delogo.png” show_in_lightbox=”off” url_new_window=”off” use_overlay=”off” animation=”left” sticky=”off” align=”left” force_fullwidth=”off” always_center_on_mobile=”on” use_border_color=”off” border_color=”#ffffff” border_style=”solid”] [/et_pb_image][et_pb_text admin_label=”Text” background_layout=”light” text_orientation=”left” use_border_color=”off” border_color=”#ffffff” border_style=”solid” module_class=”smallsidebar”]…
-
KnowIT Server Changelog
[et_pb_section admin_label=”section”][et_pb_row admin_label=”row” make_fullwidth=”off” use_custom_width=”off” width_unit=”on” use_custom_gutter=”off” custom_padding=”6em|||” padding_mobile=”off” allow_player_pause=”off” parallax=”off” parallax_method=”off” make_equal=”off” parallax_1=”off” parallax_method_1=”off” parallax_2=”off” parallax_method_2=”off” column_padding_mobile=”on”][et_pb_column type=”1_4″][et_pb_image admin_label=”Image” src=”https://blog.digitalendpoint.com/wp-content/uploads/2015/12/delogo-1.png” show_in_lightbox=”off” url=”http://digitalendpoint.com/” url_new_window=”on” use_overlay=”off”…

